Intel today announced a new security capability, dubbed as Intel Control-Flow Enforcement Technology (Intel CET), which will be first available on the upcoming mobile processor ‘Tiger Lake’. Intel’s CET plans to deliver CPU-level security capabilities to help protect against common “malware attack” methods, which have been challenging to mitigate in the past, even with software.
The semiconductor giant plans to debut a new ‘hardware-based’ security feature, called Intel Control-Flow Enforcement Technology, in future processors, starting with the Tiger Lake laptop chips, to protect against a class of malware.
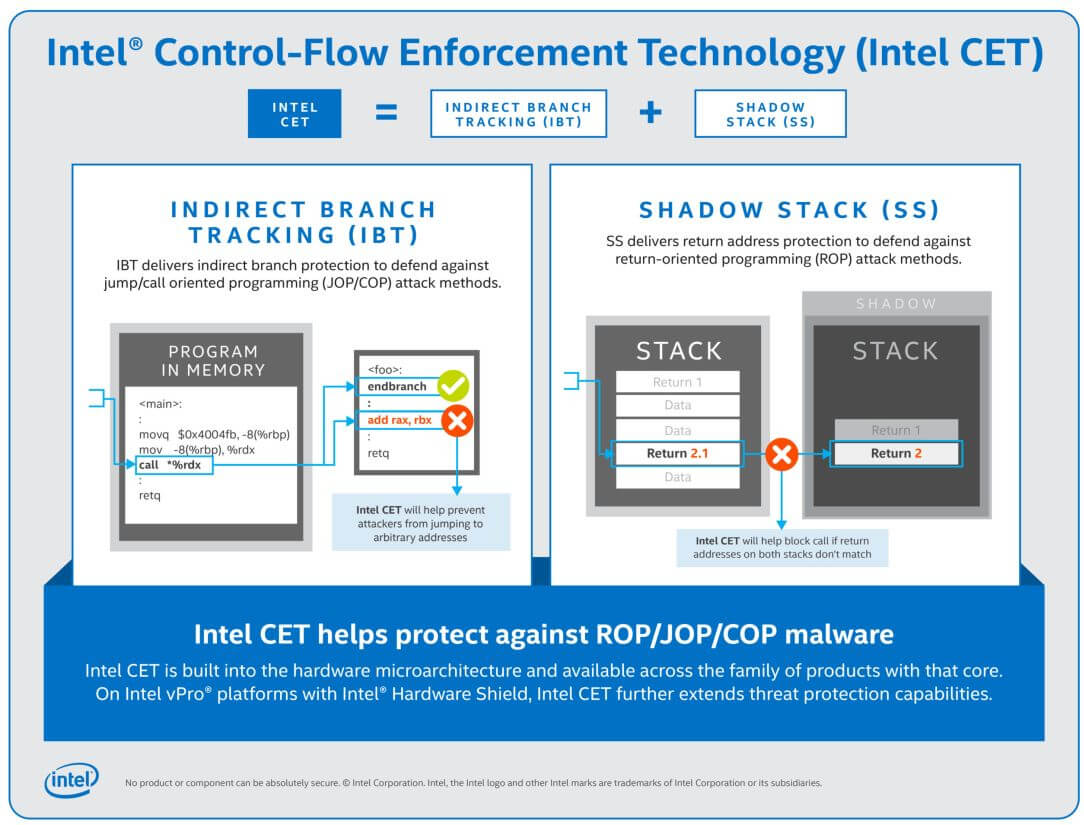
The company said Intel CET is designed to protect against the misuse of legitimate code through control-flow hijacking attacks, widely used techniques in large classes of malware. Intel CET offers software developers two key capabilities to help defend against control-flow hijacking malware, one is indirect branch tracking and the other is called shadow stack.
‘Indirect branch tracking’ delivers indirect branch protection to defend against jump/call-oriented programming (JOP/COP) attack methods. ‘Shadow stack’ on the other hand delivers return address protection to help defend against return-oriented programming (ROP) attack methods. These types of attack methods are part of a class of malware referred to as memory safety issues, and include tactics such as the corruption of stack buffer overflow and use-after-free.
Intel’s upcoming Tiger Lake CPUs will be the first to have hardware-based Malware protection. According to the Santa Clara chipmaker, Tiger Lake, which will be sold in laptops under the Intel Core brand, would be the first family of processors to use this new Intel Control-Flow Enforcement Technology. Future server and desktop processors will also get this feature, including future vPro processors, as part of the company’s remote IT management platform.
It will be enabled through a feature in Windows 10 called ‘Stack Protection’, which Intel said is now available in Microsoft’s latest preview build as part of the Windows Insider Program. Intel said it is also working with compiler vendors and software developers to support Intel Control-Flow Enforcement Technology, or CET for short. More than 50 laptop designs coming out this holiday season are expected to use Intel’s Tiger Lake processors, the successor to last year’s Ice Lake, Intel’s CEO Bob Swan said in April.
Tom Garrison, vice president of Intel’s Client Computing Group and general manager of Security Strategies and Initiatives, told that Intel Control-Flow Enforcement Technology, or CET, is a set of “silicon-level instructions” that targets a malware type known as control-flow hijacking that has been traditionally difficult to mitigate through software, which is what prompted Intel to develop the feature.
According to TrendMicro’s Zero Day Initiative (ZDI), 63.2 percent of the 1,097 vulnerabilities disclosed by ZDI from 2019 till today were memory safety related. These malware types target operating systems (OS), browsers, readers and many other applications. It takes deep hardware integration at the foundation to deliver effective security features with minimal performance impact.
“Intel was the first to tackle these complex security challenges, and we remain committed to working with the industry to drive security innovation. We recognized that scaling OS and application adoption to truly solve the problem would require industry wide collaboration. To accelerate adoption, we published the Intel CET specifications in 2016,” said Tom Garrison, vice president of the Client Computing Group and general manager of Security Strategies and Initiatives, Intel.
Intel said it has been working closely with Microsoft to prepare Windows 10 and developer tools so applications and the industry at large can offer better protection against control-flow hijacking threats.
Microsoft’s upcoming support for Intel CET in Windows 10 is called “Hardware-enforced Stack Protection” and a preview of it is available in Windows 10 Insider Previews. This new Hardware-enforced Stack Protection feature only works on chipsets with Intel CET instructions. It relies on a new CPU architecture that is compliant with Intel CET specifications. For applications running on an OS that supports Intel CET, Intel said users could expect detailed guidance from its partners on how applications opt-in for protection.
Intel said the significance of Intel CET is that it is built into the microarchitecture and available across the family of products with that core. While Intel vPro platforms with Intel Hardware Shield already meet and exceed the security requirements for Secured-core PCs, Intel CET further extends advanced threat protection capabilities. Intel CET is also expected to be available in future desktop and server platforms.
“As our work here shows, hardware is the bedrock of any security solution. Security solutions rooted in hardware provide the greatest opportunity to provide security assurance against current and future threats. Intel hardware, and the added assurance and security innovation it brings, help to harden the layers of the stack that depend on it,” added Garrison. “The security of our products is an ongoing priority, not a one-time event. Together with our partners and customers, we continue to build a more trusted foundation for all computing systems”.
Hello, my name is NICK Richardson. I’m an avid PC and tech fan since the good old days of RIVA TNT2, and 3DFX interactive “Voodoo” gaming cards. I love playing mostly First-person shooters, and I’m a die-hard fan of this FPS genre, since the good ‘old Doom and Wolfenstein days.
MUSIC has always been my passion/roots, but I started gaming “casually” when I was young on Nvidia’s GeForce3 series of cards. I’m by no means an avid or a hardcore gamer though, but I just love stuff related to the PC, Games, and technology in general. I’ve been involved with many indie Metal bands worldwide, and have helped them promote their albums in record labels. I’m a very broad-minded down to earth guy. MUSIC is my inner expression, and soul.
Contact: Email