Security researchers at Eclypsium have discovered a new severe vulnerability that affects the bootloader process used by virtually every Linux system in use, and almost every Windows OS PC device using ‘Secure Boot’ with Microsoft’s standard Unified Extensible Firmware Interface (UEFI) certificate authority. A high-rated security vulnerability found in the Secure Boot function of the majority of laptops, desktops, workstations and servers has been confirmed.
The vulnerability, tracked as CVE-2020-10713 and dubbed BootHole, has a CVSS score of 8.2 and researchers at Eclypsium say it affects all operating systems that use GRUB2 with Secure Boot, which is a mechanism designed to protect the boot process from outside attacks. In fact, the research firm says that the flaw impacts systems that use Secure Boot even if they’re not using GRUB2. Billions of devices are vulnerable, from laptops, desktop PCs, servers, and workstations, and some special-purpose equipment used in industrial, healthcare, financial, and few other industries.
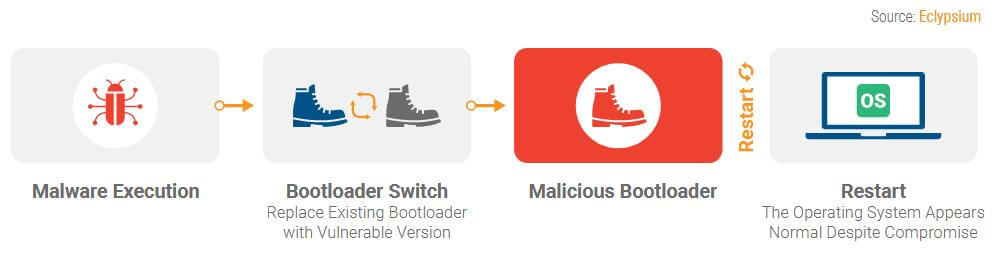
The vulnerability, codenamed as BootHole, can allow attackers to tamper with the boot-loading process that precedes before starting up the actual operating system (OS). This process relies on components known as ‘bootloaders’ that are responsible for loading the firmware of all computer hardware/system components on which the actual OS runs.
BootHole appears to be vulnerability in GRUB2, which is one of the most popular bootloader component. Basically, GRUB2 is used as the primary bootloader for all major Linux distros, but it can also boot and is sometimes used for Windows, macOS, and BSD-based systems as well. If successfully exploited, BootHole opens up Windows and Linux devices to arbitrary code execution during the boot process, even when ‘Secure Boot’ is enabled, which explains the severity of this bug. This could mean that an attacker could gain persistence for stealthily installed malware and give them a near total control over the effected device/system, according to Eclypsium.
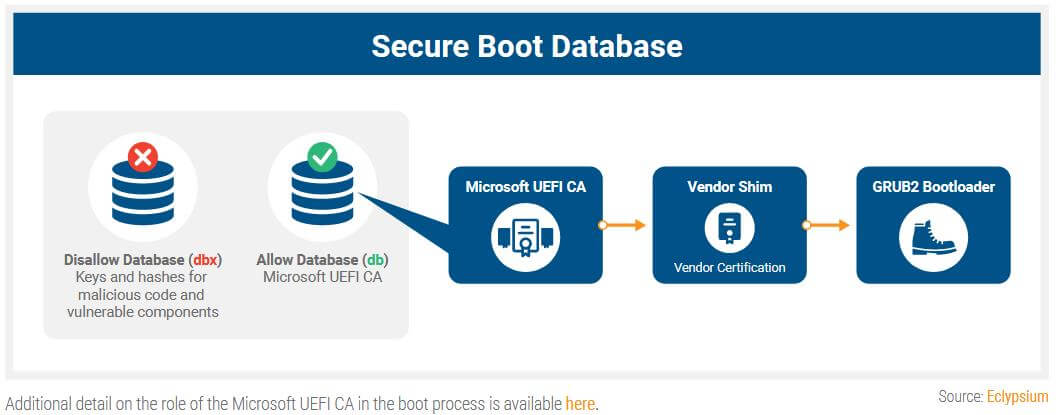
“Almost all signed versions of GRUB2 are vulnerable, meaning virtually every Linux distribution is affected,” Eclypsium firm explained in its report. “In addition, GRUB2 supports other operating systems, kernels and hypervisors such as Xen. The problem also extends to any Windows device that uses Secure Boot with the standard Microsoft Third Party UEFI Certificate Authority.”
BootHole has been described as a ‘buffer overflow’ flaw related to how GRUB2 parses its own grub.cfg configuration file. An attacker can then modify this file, which appears to be an unsigned text file typically found in the EFI system partition, to ensure that their malicious code is executed in the UEFI environment, before the actual operating system/OS is loaded. This enables the attacker to run malware, modify the whole boot process, or directly patch the operating system’s kernel.
“Mitigation will require new bootloaders to be signed and deployed, and vulnerable bootloaders should be revoked to prevent adversaries from using older, vulnerable versions in an attack. This will likely be a long process and take considerable time for organizations to complete patching,” the security company explained in its blog. According to Eclypsium, “Mitigation is complex and can be risky and will require the specific vulnerable program to be signed and deployed, and vulnerable programs should be revoked to prevent adversaries from using older, vulnerable versions in an attack. The three-stage mitigation process will likely take years for organizations to complete patching.”
However, once a system has been compromised it will appear to operate as normal even though malware has complete access to the whole system/OS. The malicious code then resides in the bootloader silently, and thus will persist even after re-installing the operating system. As explained before, the vulnerability (CVE-2020-10713) has been assigned a CVSS score rating of 8.2, meaning attackers can exploit the vulnerability to gain near-total access to any effected device.
Eclypsium says BootHole can be (ab)used to tamper with the bootloader, or even replace it with a malicious or vulnerable version. More importantly, Eclypsium firm says that a BootHole attack also works even when servers or workstations have the ‘Secure Boot’ enabled. As you already know, Secure Boot is a process where the server/computer uses cryptographic checks to make sure the boot process loads only cryptographically signed firmware components. But BootHole works even with Secure Boot enabled because for some devices and OS setups, the Secure Boot process does not cryptographically verify the grub.cfg file, hence allowing attackers to tamper with its content.
The GRUB2 (Grand Unified Bootloader) handles loading of the system and transferring control to the OS during boot time, and if this whole loading process is compromised, attackers can gain full access and control of the effected system. Eclypsium says it has been notifying the entire hardware and software ecosystem about BootHole. The company estimates that almost every Linux distribution is impacted by this vulnerability, as all use GRUB2 bootloaders that read commands from an external grub.cfg file. “To date, more than 80 shims are known to be affected,” Eclypsium said. Shims are actually components that allow vendor/OEM-specific firmware code to interact with GRUB2. “In addition to Linux systems, any system that uses Secure Boot with the standard Microsoft UEFI CA is vulnerable to this issue,” the research team added.
IT companies are expected to release patches to address BootHole in their products, including firms like Microsoft, UEFI Security Response Team (USRT), Oracle, Red Hat (Fedora and RHEL), Canonical (Ubuntu), SuSE (SLES and openSUSE), Debian, Citrix, HP, VMware, and also including OEMs, and Software vendors. Eclypsium researchers expect patching to take a long while, as fixing ‘bootloader’ bugs is usually a very complex process due to the multitude of components, and nature of advanced cryptography involved in this whole process.
Hello, my name is NICK Richardson. I’m an avid PC and tech fan since the good old days of RIVA TNT2, and 3DFX interactive “Voodoo” gaming cards. I love playing mostly First-person shooters, and I’m a die-hard fan of this FPS genre, since the good ‘old Doom and Wolfenstein days.
MUSIC has always been my passion/roots, but I started gaming “casually” when I was young on Nvidia’s GeForce3 series of cards. I’m by no means an avid or a hardcore gamer though, but I just love stuff related to the PC, Games, and technology in general. I’ve been involved with many indie Metal bands worldwide, and have helped them promote their albums in record labels. I’m a very broad-minded down to earth guy. MUSIC is my inner expression, and soul.
Contact: Email